With cyber-crimes looming large, effectively securing sensitive data has emerged a big challenge for government agencies and military establishments. As they embrace new technologies, newer threats keep pace. Though the IT infrastructure of government agencies face both external and internal security threats, of late, internal threats seem to be far more alarming as many of the reported security incidents have been caused by malicious insiders having authorized or unauthorized privileged access to the government IT resources. Analysis by IT experts has revealed that insider threat is growing at unprecedented rates. This paper analyzes how insider threats stem in government agencies, the ways to tackle the challenge and also brings out the importance of controlling access to Privileged Passwords.
As government agencies, military and other federal departments are increasingly leveraging the power of information technology to manage their activities and offer various services, information security has become the top concern. With cyber-crimes looming large, effectively securing sensitive data has emerged a big challenge for government agencies.
While the effect of cyber-threats to private establishments is limited to financial and reputation loss, security incidents in government agencies might jeopardize even National Security. Nevertheless, just as private establishments, government agencies are also tasked with building up public trust through integrity and confidentiality of information while serving the citizens.
A recent study by Computer Emergency Response Team (CERT) states:
"The number of cases of insider IT sabotage in the IT sector is quite striking. The government sector is second in number of insider IT sabotage attacks"
-- Common Sense Guide to Prevention and Detection of Insider Threats 3rd Edition - Version 3.1, Dawn Cappelli, Andrew Moore, Randall Trzeciak and Timothy J. Shimeall, CERT, Carnegie Mellon University.
CERT® is a registered Service Mark of Carnegie Mellon University
As a result, there is a greater sense of caution and necessity among the government establishments at all levels to protect sensitive information and secure their IT infrastructure. As government agencies embrace new technologies, newer threats keep pace. Adoption of cloud computing and virtualization has made enterprise security all the more difficult and highly important.
Transparency in transactions being the hallmark of government functioning, many details are required to be exposed to the public. Government agencies, by their very nature, deal with an enormous amount of sensitive data/information. All these make the Government establishments vulnerable to data breaches and cyber-attacks from amateur and expert hackers.
Internal Threats - Threat to information security does not always stem from outside. It could well be generating right inside the organization. Disgruntled staff, greedy techies, tech-savvy contractors and sacked employees could act with malicious intent and misuse privileged access. The business and reputation of some of the world's mightiest organizations, including many government agencies have been shattered in the past by a handful of malicious insiders.
Traditionally, keylogger trojans (which monitors keystrokes, logs them to a file and sends them to remote attackers), cross-site scripting (which enables malicious attackers to inject client-side script into web pages viewed by other users and exploit the information to bypass access controls) and viruses have mostly acted as the external security attack channels.
However, of late, internal threats seem to be far more alarming as many of the reported security incidents have been caused by malicious insiders having authorized or unauthorized privileged access to the government IT resources. Malicious insiders can potentially misuse the privileged access to IT resources and wreak havoc by stealing, manipulating and destroying sensitive data.
In fact, analysis by IT security experts reveals that unauthorized access to IT resources by malicious insiders is the fastest growing security threat for government agencies. And, the insider threat is growing at unprecedented rates.
While security devices, intrusion detection solutions and other applications help combat the external threats, effectively mitigating insider threats is a huge challenge and mandates a multi-pronged strategy. Before discussing the ways to combat insider threats in government agencies, it is worthwhile to delve into the causes.
In many of the reported cyber-sabotages, misuse of privileged access to critical IT infrastructure and stolen identities have served as the 'hacking channel' for the malicious insiders to wreak havoc on the confidentiality, integrity and availability of the organization's information systems.
Privileged passwords are aptly called as 'keys to the kingdom' as they enable the users to get virtually unlimited access and full controls to the IT resources such as servers, databases, network devices and IT applications. Those who login through the privileged mode could access absolutely anything with ease.
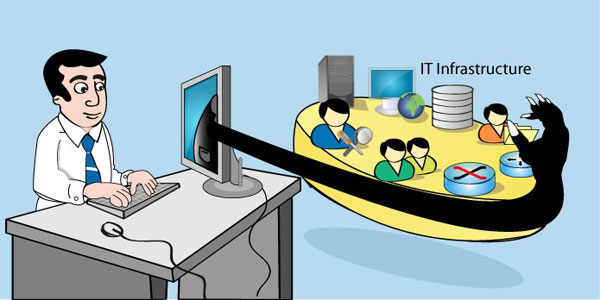
Typically, government agencies have thousands of privileged passwords, majority of which are used in shared environment. That means, a group of administrators use the common privileged account to access the resource. In reality, the passwords are just left open to be managed by the group. The privileged accounts are accessible to all the members of a team. The 'shared' nature grants anonymity, which enables misuse without a trace and as a result, privileged passwords remain virtually in utter disorder.
It is increasingly becoming clear that improper management of the privileged/administrative passwords could potentially remain at the root of a good number of security threats. In fact, a recent analysis by experts reveals that more than 80 per cent of the internal attacks had stemmed from people having access to privileged identities.
Thus, administrative passwords are insecurely shared and lie scattered in the organization leaving little scope for any internal controls. The haphazard style of password management makes the organization a paradise for hackers - internal or external. Many security incidents and data breaches might actually stem from lack of adequate password management policies and strict internal controls.
Not all security incidents and data breaches could be prevented or avoided; But, the ones that happen due to lack of effective internal controls are indeed preventable.
Combating the sophisticated insider threats in government agencies mandates preventive steps and a multi-pronged strategy - controlling access to resources, enforcing security policies, adhering to best practices, monitoring events for real-time situational awareness, detecting vulnerabilities, tracking changes, ensuring compliance to regulations, analyzing actions, automated user provisioning and de-provisioning and a host of other activities.
It is pertinent to quote here one of the best practice approaches suggested by CERT. Advocating the implementation of strict password and account management practices, CERT states:
"No matter how vigilant an organization is in trying to prevent insider attacks, if their computer accounts can be compromised, insiders have an opportunity to circumvent both manual and automated controls. Password and account management policies and practices should apply to employees, contractors, and business partners. They should ensure that all activity from any account is attributable to the person who performed it."
One of the effective ways to mitigate insider threats is to automate the entire life cycle of Privileged Access Management enforcing best practices. Privileged Password Management solutions act as the alternative for the traditional, inefficient and insecure password management processes. They provide an automated, policy-driven solution for shared administrative password management and help achieve high level of security for the data.
One of the effective ways to mitigate insider threats is to automate the entire life cycle of Privileged Access Management enforcing best practices
Privileged Password Managers help government agencies safeguard their data and thereby avoid security incidents in multiple ways:

If you are looking for a solution to bolster the security of your IT infrastructure and in turn, protect the critical data, ManageEngine Password Manager Pro would be the ideal choice. Password Manager Pro (PMP) is a web-based, secure vault for storing and managing shared sensitive information such as passwords, documents and digital identities of enterprises.
It helps control the access to shared administrative passwords of any 'enterprise resource' such as servers, databases, network devices, applications etc. PMP enables IT managers to enforce standard password management practices.
Researchers repeatedly point out that insider threats and identity theft incidents are on the rise and it will only keep growing due to many reasons, including economic situation, social factors and technological advancements that make the tech-savvy criminals more creative every passing day.
Achieving data security is indeed a continuous journey, in which preventive measures that offer comprehensive protection take precedence. With insider threats looming large, taking preventive action is the need of the hour. Use Password Manager Pro and Stay Secure!
 |
"Password Manager Pro is an excellent choice for password management. The application is reliable, dependable, and the support is fantastic. I am confident in the security the application provides at a fraction of the cost of alternatives"
- Don Garvey, Director of Operations BlueVault, USA
|