Administrative passwords are literally ‘aplenty’ in enterprises of all sizes. They are mostly insecurely shared and lie scattered in the enterprise leaving little scope for any internal controls. This white paper discusses the security threats associated with the password sharing in enterprises. Though the security and operational problems caused by shared administrative passwords are so obvious, no organization can afford to eliminate them altogether. The ways to tackle this challenge, the importance of effective Shared Account Password Management and the need for enterprise password management solutions have been dealt with.
Administrative passwords are omnipresent and all pervasive in enterprises of all sizes - big and small. Organizations depend on a variety of IT resources to sustain their businesses. Servers, databases, network devices and numerous other IT applications are controlled through administrative passwords, which are aplenty.
Needless to say, administrative passwords are very powerful and accord unlimited privilege to the users. Those who login through the privileged mode could access absolutely anything with ease.
Typically, enterprises have thousands of privileged passwords, majority of which are used in shared environment. That means, a group of administrators use the common privileged account to access the resource. The privileged accounts are accessible to all the members of a team.
Apart from the 'officially shared' passwords, users often tend to reveal administrative passwords to their colleagues for some reason or other. The most common reason for such an 'unofficial share' is to cater to an emergency on one's absence - IT Manager revealing the password to a senior member when he has gone on vacation.
Whether it is official or casual, sharing of privileged passwords in enterprises could have disastrous repercussions on the security of the enterprise. Mismanagement of administrative passwords leads to information theft, manipulations and sabotage without a trace.
It is always good to avoid sharing of administrative passwords. Unfortunately, it is just an ideal situation. Practical needs are mostly the opposite. Business requirements demand selective sharing of passwords with others and yet not compromising on enterprise security. Thus, enterprises find themselves in a catch-22 situation!
Administrative/Privileged passwords are literally 'aplenty' in enterprises. Just a single instance of a database could have as many as 30 administrative accounts. Servers, switches, routers and any other hardware or software, could have equally large number of administrative passwords. So, easily, even a small enterprise having a modest number of devices and applications will have thousands of privileged passwords.
A group of administrators in a team would require access to the same set of privileged passwords and hence, in reality, the passwords are just left open to be managed by the group.
Most of the administrators will have access to all the privileged accounts. This is called 'shared environment', where privileged passwords remain virtually in utter disorder.
Developers, help desk technicians and in certain cases, some third party vendors who require access to privileged passwords purely on temporary basis, are supplied with the required passwords mostly orally or through emails. There is no process to revoke temporary access and reset the password after the temporary usage, which leaves a big security hole.
It is quite common to see administrators assigning some familiar words or short phrases as passwords, for ease of use. The passwords are maintained in text files, spread sheets, homegrown tools or even in physical vaults. And, it is not uncommon to see UNIX administration team having full access to the Windows passwords, developers having full access to database passwords and so on.

Apart from the shared accounts, even the 'personalized accounts' of the top brass in the IT team are often revealed to the team members to tackle emergency issues. Many surveys by industry analysts have time and again pointed out that administrators often tend to casually 'tell' the passwords to their colleagues to carry out certain work in proxy.
Thus, administrative passwords are insecurely shared and lie scattered in the enterprise leaving little scope for any internal controls.

The security and operational problems caused by shared administrative passwords are so obvious; but, no organization can afford to eliminate them altogether. Without compromising security, shared administrative passwords have to be used.
All the threats associated with the shared administrative passwords, can be easily mitigated using a good 'Shared Account Password Management' (SAPM) software available in the market. The SAPM solutions act as the alternative for the traditional, inefficient and insecure password management processes. They provide an automated, policy-driven solution for shared administrative password management.
SAPM tools have emerged as a best-practice choice for managing shared-account passwords across all sizes of organization and all vertical industries. They provide efficient and effective password management for shared superuser and firecall accounts in a robust, controlled and accountable manner, enabling any enterprise to meet regulatory compliance requirements for restricted access and individual accountability".
It is pertinent to quote here a recent research report by Gartner:
(Source: Gartner, Inc., "MarketScope for Shared-Account/Software-Account Password Management", Ant Allan, Perry Carpenter, 16 June 2009).
he SAPM solutions enable enterprises to establish a secure process for the entire life-cycle of administrative password management. They help securely store administrative passwords in a centralized vault and provide access through a web-interface. Access controls are well-defined - users will be allowed to retrieve only those passwords that are allotted to them; NOT all passwords of the enterprise.
All passwords will have well-defined ownership - the owner alone will have absolute privilege on the passwords. Unless the owner shares the passwords, no other user will be permitted to view the passwords. The owner can share the passwords with others granting granular permission for various actions - password retrieval, reset etc., If an administrator leaves the organization, de- provisioning of passwords can be done instantly.
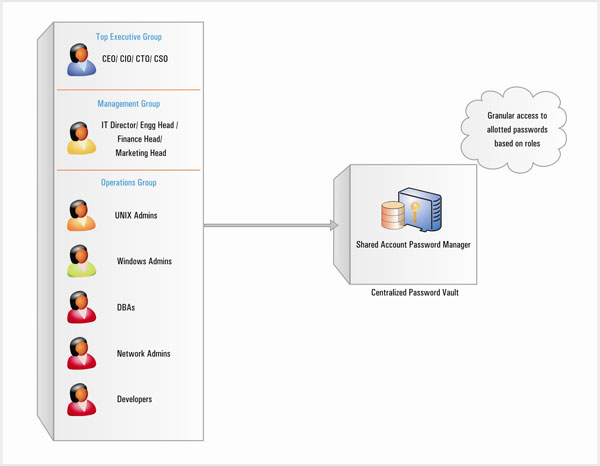
At any point of time, one can get a clear picture of 'who' has access to 'what' resources. When an administrator accesses a shared privileged password, audit trails are generated.
Thus the anonymity and the disorder created due to the traditional process are completely eliminated. If something goes wrong, user actions could be easily traced to individual users.
The SAPM solutions help establish a secure connection to the target systems and reset the passwords whenever required or automatically through scheduled tasks.
In summary, with an SAPM solution in place, IT Managers can ensure strict internal controls and comply with regulations; enforce standard policies, processes and practices. Whatever be the number of privileged passwords - thousands or millions, storing, sharing, accessing and changing them will be a breeze. Security threats arising due to password sharing are completely eliminated.