Configuring Firewall to Fetch Configuration and Unused Rules
In a Firewall device, there could be numerous rules/access-list defined to secure the network from external attacks. Out of the rules/access-list configured, there could be certain rules which would be most used and certain which are least used or never used. Firewall Analyzer captures the most used rules in the Top Used Rules as they would be available in the logs generated by Firewall. But, to get the Unused Rules, one needs to configure the Firewall Analyzer to fetch the complete rules from the device. Once, Firewall Analyzer fetches the complete rules configured in the Firewall, it can provide the Unused Rules view.
To view Unused Firewall Rules, configure the Firewall Analyzer by following the steps given below:
- In the Firewall Analyzer web client, select the Settings tab.
- In Settings screen, select the System Settings > Device Rule link. Device Rule Info page appears.
- On the top, there are links provided to add device info to fetch rules and
to delete the device info. The links are:
Device Rule Info
Devices Details
After entering and saving the Device Info values through the Firewall Analyzer GUI, the device, with details to fetch rules, is listed in the Device Details table. The details of the columns of the Device Details table are:
Device Details |
Description |
| Status |
The status of fetching device rules/access control of the Firewall device |
| Devices Name |
The names of the devices for which the rules will be fetched |
| Virtual FWs |
For multi (vdom/context) Firewallls, this will display the number of vdoms/contexts associated to this specific device rule. Clicking on the count will show the details of the vdoms/contexts individually. Refer the screen shot below. |
| Edit |
An icon to edit the details of the rules fetching info of the device. Click icon to edit the device info. |
| View Rules |
An icon to view the rules fetched from the device. Click icon to view the device rules. |
| Unused Rules |
An icon to view the rules fetched from the device, which were not used. Click icon to view the unused rules of the device. |
| Compliance Reports |
The Compliance Reports related to Firewall Security Audit and Configuration Analysis. The report is available on clicking the link and the link text shows the time the compliance report was generated. You can instantly generate the Compliance report by clicking the icon. |
| View Config Changes |
The configuration changes of the Firewall devices are reported. The report is available on clicking the link and the link text shows the time the configuration change report was generated. You can instantly fetch the current configuration change report by clicking the icon. |
| Last Update On |
The time when the rules of the device were updated last. |
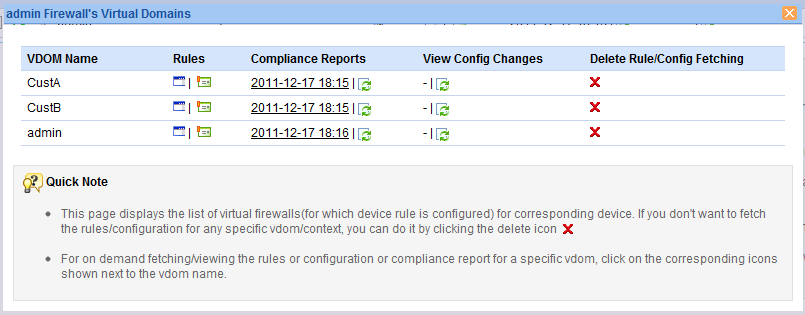
Virtual FWs
- When you click the Virtual FWs number displayed in the Device Details list you will see the details of the virtual domains in a pop-up window which will provide you with all the options (see screen shot below).
Add Device Info
- Click the Add Device Info link to add the device information to fetch the rules and configurations using Telnet, Telnet-TFTP, SSH, SSH-TFTP, SCP. The Enter Device Details screen opens up.
- Select the Firewall device in the Select Device drop down list.
- In the Fetch Rules/Config drop down list, there will be two options to fetch rules and configurations
- From Device
- From File
Select the option as per your requirement.
Next, there will be two tabs, Credentials and Choose Report.
The Credetials tab
You can configure the individual device credentials to fetch the rules and configuration from the device or you can create a common profile of device credential which can be used for a group of devices to fetch rules.
|
System requirement: For Change Management, 1 GB RAM is required
Fetching the rules directly from the device is supported for the following devices only:
- Cisco
- Fortigate
- Netscreen
- Juniper SRX
For the rest of the devices, please use the Fetch Rules/Config > From File option. |
Fetch Rules/Config > From Device
- Select the protocol (Telnet, Telnet-TFTP, SSH, SSH-TFTP, SCP) in the Protocol drop down list.
- Select the profile in the Use Profile drop down list. If there is no profile available or you want to create and use a new profile, click New Profile link besides the combo box.
- Enter the Device Info. The Device Info has been split into two sections:
- Primary Info - deal with parameters that are necessary to establish communication with the device. Details such as Login Name, Password, Prompt, Enable UserName, Enable Password and Enable Prompt are classified as basic details.
- Secondary Info - certain parameters usually take standard values. All such parameters have been classified under 'Secondary Info'. Port, login prompt, enable user prompt, password prompt, enable password prompt values are usually assigned with certain Standard Values by default. Such standard values have been filled for these parameters. Most of the devices would work well with these values and you need not edit these details unless you want to provide different set of details.
Primary Info
Device Info
|
Description |
Login Name
|
While establishing connection with a device, if the device asks for a Login Name, set a value for this parameter. This parameter is Optional. |
Password
|
To set the Password for accessing the device. |
Prompt
|
The prompt that appears after successful login. |
| Banner Input |
The input for banner during the CLI operation to proceed further |
| Banner Prompt |
The banner prompt that appears during the CLI operation |
Enable UserName
|
When entering into privileged mode, some devices require UserName to be entered. Provide the username if prompted; otherwise leave this field empty. |
Enable Password
|
This is for entering into privileged mode to perform configuration operations like backup/upload. This parameter is mandatory. |
| Enable Prompt |
This is the prompt that will appear after going into enable mode. |
|
Both Primary and Secondary credentials (Login Name and Password) of the Firewalls are encrypted and stored in the Firewall Analyzer. |
Secondary Info
Click the link Secondary Info to view/enter values for these parameters. All the parameters are usually assigned with certain Standard Values by default. Such standard values have been filled for these parameters. Most of the devices would work well with these values and you need not edit these details unless you want to provide different set of details.
Device Info
|
Description |
| IP Address |
IP Address of the Firewall device to which the Firewall Analyzer will connect through FTP. See Note below. |
| Port (Telnet, Telnet-TFTP, SSH, SSH-TFTP, SCP) |
Port number: 23 (for Telnet, Telnet-TFTP) and 22 (for SSH, SSH-TFTP) by default. |
Login Prompt
|
The text/symbol that appears on the console to get the typed login name is referred as login prompt. For example, Login: |
Password Prompt
|
The text displayed on the console when asking for password. For example, Password: |
Enable User Prompt
|
The text displayed on the console when asking for Enable UserName. For example, UserName: |
Enable Password Prompt
|
The text displayed on the console when asking for password. For example, Password: |
- The command to be executed, to fetch the Firewall rules is displayed in the Command field.
- Click Test button, to test the validity of the device info.
The Choose Report tab
- Select Fetch Rules from the device check box to fetch the rules from the Firewall device.
If commands are not available to fetch rules from the device, Choose File button automatically appears besides the select item. If the file is not yet selected, 'No file
chosen' message appears besides the button. If it is not supported for the particular device [ Not Supported ] messages appears besides the select item.
- Select Generate Compliance Report check box to generate Firewall Compliance report. If commands are not available to fetch configurations from the device, Choose File button automatically appears besides the select item. If the file is not yet selected, 'No file
chosen' message appears besides the button. If it is not supported for the particular device [ Not Supported ] messages appears besides the select item.
|
In the Fetch Rules from the device section, if the following message appears: 'Unable to generate compliance report. Reason: Failed to locate Nipper. Click here to enable it'. Carry out the procedure given at the end of the document. |
- Select Generate Change Management Report check box to generate configuration change management report. In this section, Notification Options and Scheduling Options, for the configuration changes of the device, are available. If commands are not available to fetch configurations from the device, there will not be any Change Management report.
- Under the
Notification Options, enter the Email address of the user(s), who need to be informed via Email when any configuration change happens, in the Mail To: text box. Click the link Click here to configure to configure mail server for Firewall Analyzer, enter the cellular phone number of the user(s), who need to be informed via SMS when any configuration change happens, in the SMS To: text box. Click the link Click here to configure to configure SMS server for Firewall Analyzer.
- Under the Scheduling Options, enter the Email address of the user(s), to whom the report to be sent via em ail when a scheduled configuration change report is generated, in the Mail To: text box. Click the link Click here to configure to configure mail server for Firewall Analyzer. Select the schedule for report generation using the Get Report for Every <1 to 31> day(s) @ <0 to 23> Hrs <0 to 50> Min. (For example: If you configure like Every 10 day(s) @ 2 Hrs 30 Min, the reports will be generated for the device, every 10 days at 02:30 AM), For the <Previous Week, Last 7 Days, Previous Month, Last 30 Days> for the selected duration. Select the report format to be sent via em ail using the
PDF, CSV radio buttons.
- Click Save button to apply the values. Click Close button to close the adding device info screen.
|
If the Firewall Analyzer is not receiving the logs directly from the Firewall device (i.e., the logs are received from a log forwarder tool), to fetch the rules from the Firewall device, configure the IP Address of the actual Firewall. Configure the IP Address, using Secondary Info > IP Address field. |
|
Generating Change Management Report is supported for the following devices:
- Cisco
- Fortigate
- Netscreen
- Juniper SRX
|
|
Getting Rules/ Configuration Information from
the individual virtual Firewalls (vdom/context)
- Add Device Info menu supports fetching the rules/configurations for the Firewall devices. It lists only the physical devices in the Select Device drop down list. It does not distinguish between vdom/context enabled Firewall and normal Firewall device. By default, both the vdom/context Firewall (if any) and the physical Firewall rules and configurations are fetched.
- If you want to fetch the rules/configurations for a selected vdom/context individually, create a separte Device Profile and associate the vdom/context to the profile for which you need the reports. Select the option 'Display Virtual Domains in the below resources list.' in Associate Profiles to Devices page. It lists both the virtual Firewalls (vdom/context) and the physical Firewall devices in the Select Device drop down list.
|
Fetch Rules > From File
- In the From File tab, you will find the two options: Import Rule File and Import Configuration File.
- In the Import Rule File option, click the Browse button to locate the file which contains the rules details of the Firewall device.
- In the Import Configuration File option, click the Browse button to locate the file which contains the complete configuration details of the Firewall device.
- Click Import button to import the rule/configuration file. Click Cancel to cancel the rules/configuration details file importing operation.
For the complete procedure to export the configuration from various Firewalls in file format, refer the Exporting Configuration Files page.
|
Rule File
- User should create a rule file containing rules details.
- The file should contain rule name, rule hash value (optional) and description only in comma separated format.
- Each rule should be in a new line.
Configuration File
- Configuration File should contain complete configuration of device in readable format.
Only for Check Point Firewall
- In the case of Check Point firewalls, there will be multiple configuration files. In that case, if you are using "From File" mode, it should be provided in the Zip file format.
- The configuration files are:
- objects.C
- objects.C_41
- objects_5_0.C
- rules.C
- rulebases.fws
- rulebases_5_0.fws
- The files are stored in the directory conf or database.
|
Delete Device Info
- To delete the Device Info from the list of Device Details table, select the check boxes of the respective Device Info entries and click the Delete Info link.
Testing the validity of device info
Device Info values entered through the Firewall Analyzer GUI should be accurate. Otherwise, Firewall Analyzer will not be able to establish connection with the device. To ensure the correctness of device info values, Firewall Analyzer provides the testing option. After entering the device info, you can test the values during which Firewall Analyzer will indicate if the values entered are valid. It will pinpoint the invalid values and you can carry out corrections accordingly.
To test the validity of device info, follow the procedure given below:
- After providing the device info, click Test button.
This updates the device info values in the database and then carries out the testing. The result of the testing will be shown in a separate window as below:
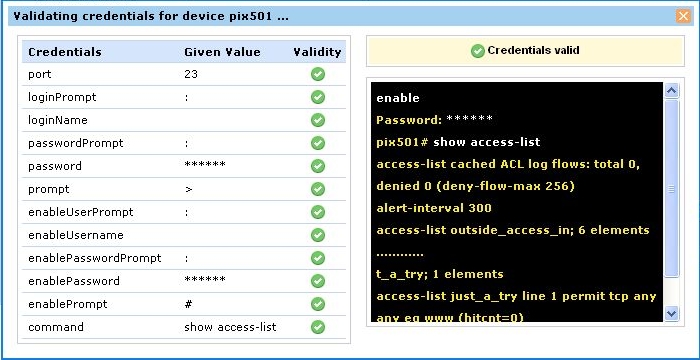
The testing result indicates valid device info values with a green 'tick' mark. The invalid values are marked as red cross marks. You need to change the invalid values. Alongside, the CLI command execution result (through which Firewall Analyzer ascertains the validity of device info values) is also displayed.
List Profile
Credential Profile Listing
Click the List Profile link to view the list device profiles to fetch the rules information from the devices. The Credential Profile Listing screen opens up.
On the top, there are links provided to add device info to fetch rules and
to delete the device info. The links are:
After creating and saving the Device Profile values through the Firewall Analyzer GUI, the profiles, edit option, view/associate profile with devices to fetch rules, is listed in the Device Profile Details table. The details of the columns of the Device Profile Details table are:
Device Profile Details |
Description |
| Profile Name |
The names of the profile, which will be used by the Firewall Analyzer to fetch the rules from the devices. |
| Edit |
An icon to edit the profile details. Click icon to edit the device profile info. |
| View/Associate Devices |
An icon to view the devices associated with the profile. Click icon to view the associated devices. If no device is associated, you will be prompted to associate a device. |
Delete Profile
- To delete the Device Profile from the list of Device Profile Details table, select the check boxes of the respective Device Profile entries and click the Delete Profile link.
Add Device Info Profile
Click the Add Device Info Profile link or New Profile link to create device info profiles to fetch the rules information from a set of common devices. The Add New Profile screen pops up.
You can configure the individual device credentials to fetch the rules from the device or you can create a common profile of device credential which can be used for a group of devices to fetch rules.
- Enter the name of the new profile in the Profile Name field. Enter the description of the profile in the Profile Description text area.
- Select the protocol (Telnet, Telnet-TFTP, SSH, SSH-TFTP, SCP) in the Protocol drop down list.
- Enter the Device Profile Info. The Device Profile Info has been split into two sections:
- Primary Info - deal with parameters that are necessary to establish communication with a common set of devices. Details such as Login Name, Password, Prompt, Enable UserName, Enable Password and Enable Prompt are classified as basic details.
- Secondary Info - certain parameters usually take standard values. All such parameters have been classified under 'Secondary Info'. Port, login prompt, enable user prompt, password prompt, enable password prompt values are usually assigned with certain Standard Values by default. Such standard values have been filled for these parameters. Most of the devices would work well with these values and you need not edit these details unless you want to provide different set of details.
Primary Info
Device Info
|
Description |
Login Name
|
While establishing connection with a common set of devices, if the devices ask for a Login Name, set a value for this parameter. This parameter is Optional. |
Password
|
To set the Password for accessing the common set of devices. |
Prompt
|
The prompt that appears after successful login. |
| Banner Input |
The input for banner during the CLI operation to proceed further |
| Banner Prompt |
The banner prompt that appears during the CLI operation |
Enable UserName
|
When entering into privileged mode, some common set of devices require UserName to be entered. Provide the username if prompted; otherwise leave this field empty. |
Enable Password
|
This is for entering into privileged mode to perform configuration operations like backup/upload. This parameter is mandatory. |
| Enable Prompt |
This is the prompt that will appear after going into enable mode. |
|
Both Primary and Secondary credentials (Login Name and Password) of the Firewalls are encrypted and stored in the Firewall Analyzer. |
Secondary Info
Click the link Secondary Info to view/enter values for these parameters. All the parameters are usually assigned with certain Standard Values by default. Such standard values have been filled for these parameters. Most of the devices would work well with these values and you need not edit these details unless you want to provide different set of details.
Device Info
|
Description |
| Port (Telnet, Telnet-TFTP, SSH, SSH-TFTP, SCP) |
Port number: 23 (for Telnet, Telnet-TFTP) and 22 (for SSH, SSH-TFTP) by default. |
Login Prompt
|
The text/symbol that appears on the console to get the typed login name is referred as login prompt. For example, Login: |
Password Prompt
|
The text displayed on the console when asking for password. For example, Password: |
Enable User Prompt
|
The text displayed on the console when asking for Enable UserName. For example, UserName: |
Enable Password Prompt
|
The text displayed on the console when asking for password. For example, Password: |
| Select Device Type |
Select the type of device (Cisco/Fortigate/Netscreen/Juniper) from the drop down list. |
- The command to be executed, to fetch the Firewall rules is displayed in the Command field.
- Click Associate Device button to assign devices to this profile. The procedure is given in the Assign Profile topic below.
- Click Save button to apply the values to the device info profile. Click Cancel to cancel the adding device profile info operation.
Assign Profile
Click the Assign Profile link to associate devices to device profiles to fetch the rules information from the devices. The Associate Profiles to Devices screen opens up.
- In the Selected Profile combo box, select the profile to be associated with the devices. If there is no profile available or you want to create and use a new profile, click New Profile link besides the combo box.
- If you want to fetch the rules/configurations from the individual virtual Firewalls (virtual domain) separately, select the option 'Display Virtual Domains in the below resources list.' It lists both the virtual Firewalls (virtual domain) and the physical devices in the Unassigned Devices & Assigned Devices list.
- Select the devices, which you want to assign/re-assign to the selected profile. All the available devices are listed in the Unassigned Device(s) list. Select the devices and click right arrow. The selected devices are moved to the Assigned Device(s) list. If you want to remove any device from the Assigned Device(s) list, select the devices and click left arrow. The removed devices will be moved back to the Unassigned Device(s) list.
- Fetch Rules
- Select whether the rules are fetched once or periodically.
- Select Once radio button to fetch the rules once.
- Select Periodic radio button to fetch the rules periodically. The periodicity option opens up. Select the periodicity of rules fetching from the combo boxes given in: Every <1 to 31> day(s) @ <0 to 23> Hrs <0 to 50> Min. (For example: If you configure like Every 10 day(s) @ 2 Hrs 30 Min, the rules will be fetched from the device, every 10 days at 02:30 AM)
- Compliance Reports
The Compliance Reports related to Firewall Rules/Policies Configuration/Changes.
- Click Map button to assign the selected devices to the selected profile. Click Cancel to cancel the assigning devices to the profile operation.
After associating the devices to Device Profiles the profiles and the associated devices are listed in the Device Profile Details table.
|
Getting Rules/ Configuration Information from
the individual virtual Firewalls (virtual domain)
If you want to fetch the rules/configurations from the individual virtual Firewalls (virtual domain) separately, select the option 'Display Virtual Domains in the below resources list.' in Associate Profiles to Devices page. It lists both the virtual Firewalls (virtual domain) and the physical devices in the Select Device drop down list. |
|
Trouble Shooting: If the following message appears in the Compliance Reports field, enable Nipper.
'Unable to generate compliance report. Reason: failed to locate nipper. Click here to enable it' |
Procedure to enable Nipper
In the Compliance Report field, the following message appears: 'Unable to generate compliance report. Reason: Failed to locate Nipper. Click here to enable it'. What should I do?
Supported Platform:
- Ubuntu 9.1.10
- Fedora 12
- OpenSuSE 11.2
- CentOS 5.5
Prerequisite:
The GNU/Linux platform requires Qt 4.5 to be installed. Your package manager system should automatically install this for you.
Steps:
- Download Nipper libraries from here according to your platform
- Install the rpm or deb according to your Operating System
- Connect to Firewall Analyzer web client and type the following URL: 'http://<host name>:8500/fw/userConfig.do'
- In that, there is an option to provide the path in which you have installed 'Nipper'. For ex: '/usr/bin/nipper'
- Click on Save link
After performing the above steps, go to Setting > Device Rule > Add Device Info, the option to generate compliance report for the device will be enabled.
|

