RADIUS Authentication
When RADIUS Authentication is enabled, end users can use their username and password from the RADIUS server to log in to ADAudit Plus.
Steps to integrate the ADAudit Plus server with RADIUS:
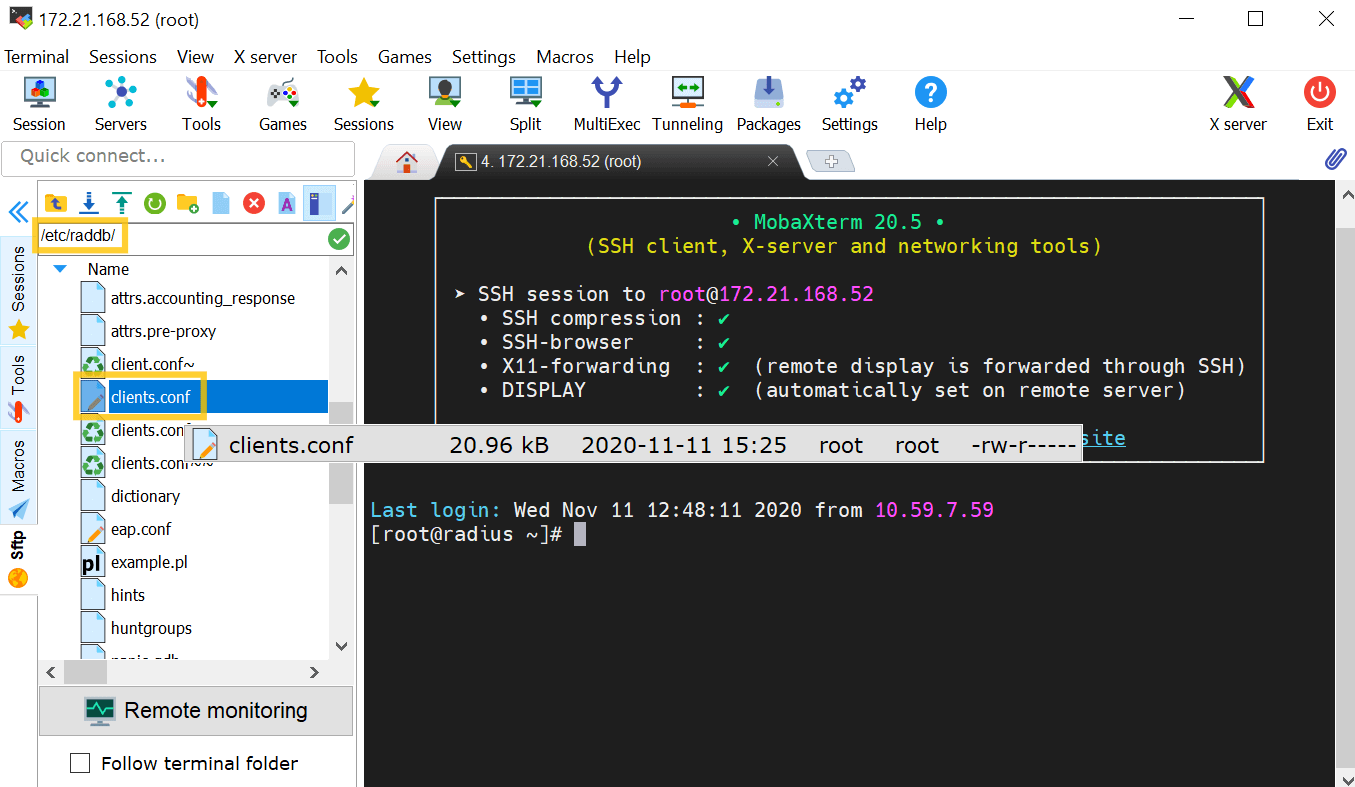
- Access your RADIUS server and find the /etc/raddb/ folder.
- Select the clients.conf file, and enter the ADAudit Plus server details.
For example, if the name of the ADAudit Plus server is "ADAP" and its IP address is 172.21.193.194, add the following entry in the clients.conf file:
client ADAP{
ipaddr = 172.21.193.194
secret = Radius@123
require_message_authenticator = no
nastype = other
}
Note: Here, "Radius@123" is the Secret Key that must be entered in the ADAudit Plus web console while configuring RADIUS.
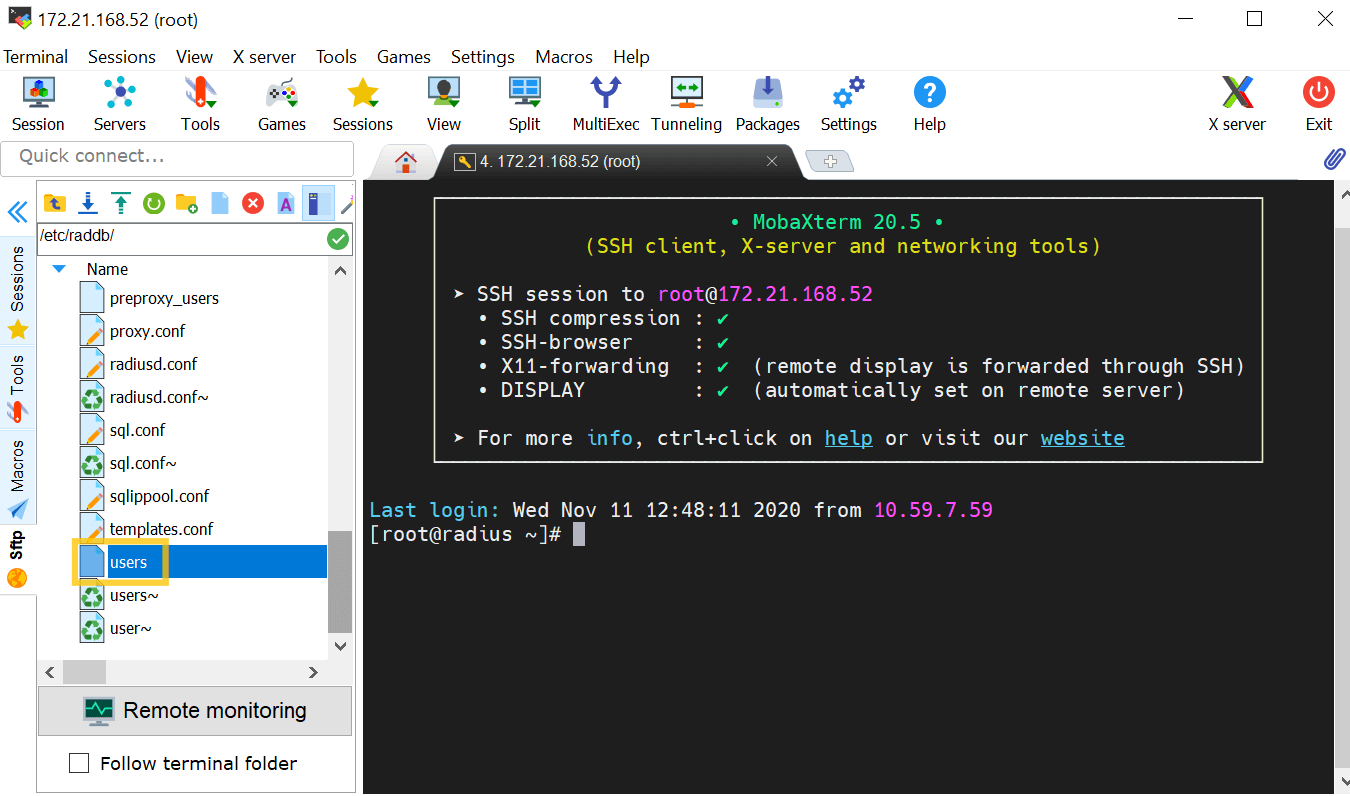
- Select users, and enter the user details.
Example format: "domain_name\\user_name" Cleartext-Password := "Test@123"
- Restart the Radiusd service using shell script.
Steps to enable RADIUS Authentication in ADAudit Plus:
- Open the ADAudit Plus web console.
- Navigate to Admin → Administration → Logon Settings, and select Two-Factor Authentication.
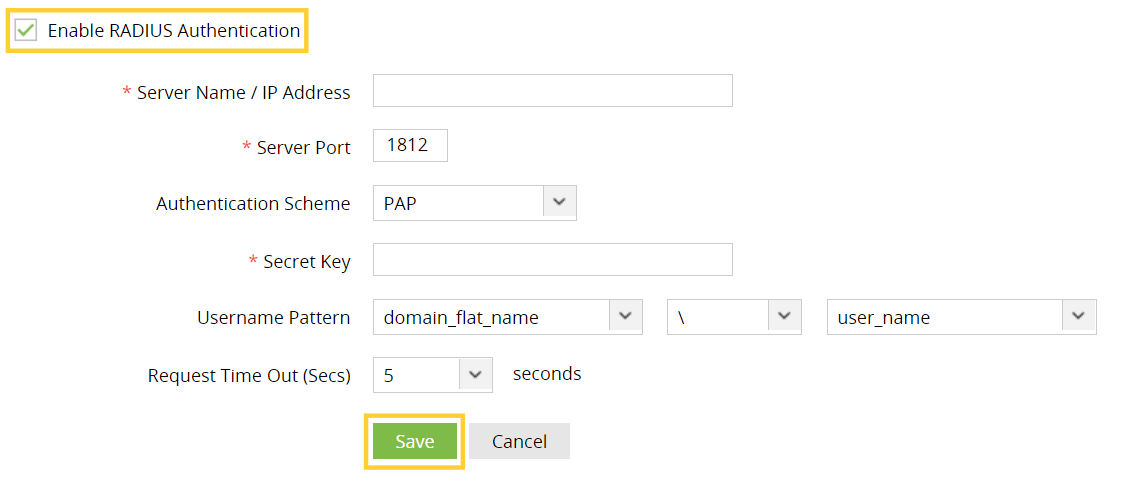
- Under RADIUS Authentication, check Enable RADIUS Authentication.
- Enter the hostname or IP address of the host where the RADIUS server is running in the Server Name / IP Address field.
- Enter the port used for RADIUS server authentication in the Server Port field (by default, RADIUS is assigned the UDP port 1812).
- Select the Authentication Scheme used to authenticate users. Choose from four protocols: Password Authentication Protocol (PAP), Challenge-Handshake Protocol (CHAP), Microsoft Challenge-Handshake Protocol (MSCHAP), or Microsoft Challenge-Handshake Protocol Version 2 (MSCHAP2).
- Enter the Secret Key that you specified while adding ADAudit Plus server as a client in your RADIUS server.
- Choose the Username Pattern, and set the Request Time Out limit.
- Click Save.